Contact
info@ergonomics-europe.com | sales@ergonomics-europe.com
+41 58 311 1000
Headquarters Zürich
Ergonomics AG | Uetlibergstrasse 132 | CH-8045 Zürich | Switzerland
Entrust offers three different solutions for cloud security. Chose those that fit your requirements.
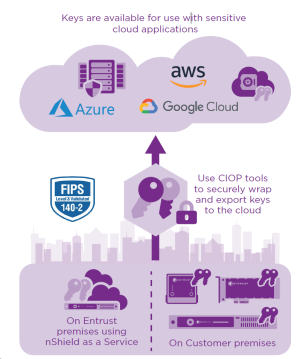 Create and control cryptographic keys in your FIPS 140-2 HSM, then securely export to the cloud.
Create and control cryptographic keys in your FIPS 140-2 HSM, then securely export to the cloud.
Provides users of public cloud services with the ability to generate cryptographic keys in their own environment. Retain control of those keys while making them available, as required, for use in the cloud of their choice.
Validated to the highest security standards, such as FIPS 140-2 and Common Criteria, Entrust nShield HSMs are ready to protect your data in even the most challenging and demanding security situations, whether on premises or in the cloud.
Cloud Integration Option Pack (CIOP) provides the tools to allow you to create your cryptographic keys using an nShield HSM then wrap and securely export them to the following cloud service providers:
For customers seeking a higher level of assurance, Microsoft offers nCipher BYOK.
The nCipher BYOK method provides additional assurances that the key permissions created at generation time are preserved during the transfer to Microsoft Azure Key Vault. In addition Microsoft make use of the nCipher Security World to restrict key use to a specified Azure region. This method does not require the purchase of CIOP. See Import HSM-protected keys for Key Vault (nCipher) for more information.
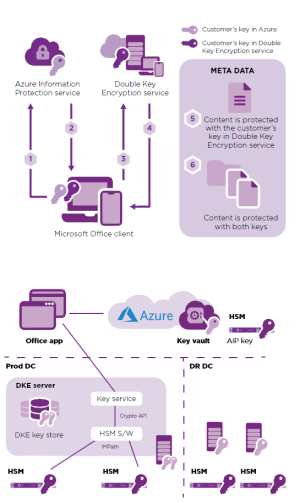 Extend control and security over sensitive data in hybrid and cloud environments
Extend control and security over sensitive data in hybrid and cloud environments
Entrust Double Key Encryption for Microsoft Azure Information Protection (AIP), offered by Entrust Professional Services, is designed to help enterprises protect their most sensitive content in Microsoft 365.
Double Key Encryption enables organizations to use hybrid-computing environments with added levels of protection, control, and assurance. As part of the Microsoft AIP offer, the solution enables enterprise customers to select who has permissions to access associated keys and decrypt content. Enterprises can store encrypted data on-premises or in the cloud, remaining unreadable to Microsoft.
Replacing Microsoft Hold your Own Key (HYOK), Double Key Encryption does not require enterprise customers to operate their own Active Directory and Rights Management servers. Instead, customers are empowered to provide their own cryptographic keys in real time.
Double Key Encryption utilizes two component cryptographic keys to protect highly sensitive data across the enterprise – a Microsoft key and a customer key.
Download the Double Key Encryption flyer.
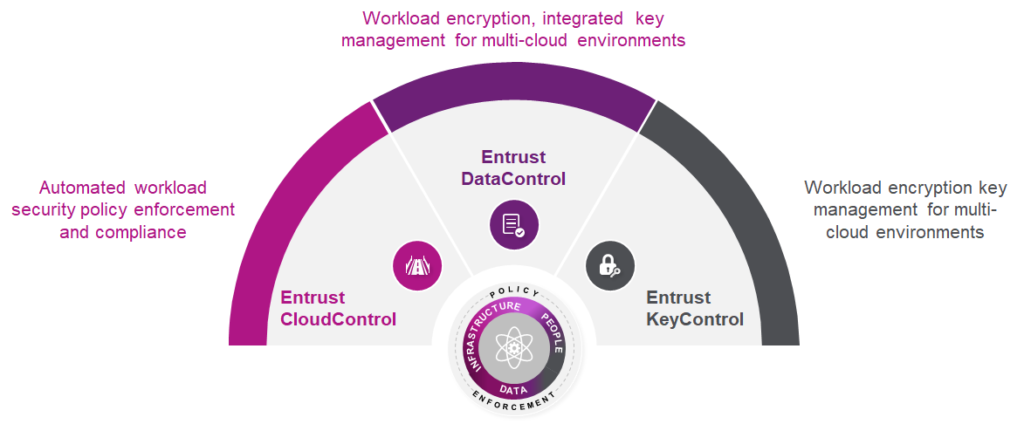
Universal key management for encrypted workloads.
Deliver enterprise scale and availability, supporting Key Management Interoperability Protocol (KMIP1)-compatible encryption agents
Managing the security of workloads in a dynamic, virtualized environment is a time-consuming and complex challenge for administrators
Encrypting workloads significantly reduces your risk of data breaches; if data does fall into the wrong hands, it is unreadable. However, managing the keys for tens of thousands of encrypted workloads is nontrivial. To ensure strong data security, keys have to be rotated frequently, and transported and stored securely. Along with the high demand for strong data security, there is an ever-increasing business need to meet regulatory requirements for PCI-DSS, HIPAA, NIST 800-53, and GDPR compliance in virtual environments.
Many virtualization platforms such as VMware vSphere do not include native key management functionality, requiring a third-party external key management server (KMS). For multi-cloud environments, key management is even more complex as many key management systems cannot interoperate between different platforms.
Enhanced multi-cloud workload encryption
KeyControl is easily upgraded to Entrust DataControl, which enables multi-cloud workload encryption and policy-based key management. It ensures policies are enforced, even when moving across cloud platforms (private and public) such as Microsoft Azure and Amazon Web Services (AWS). DataControl ensures that data within each VM is securely encrypted (AES-128/256-bit) throughout its lifecycle: from installation, upon boot, until each workload is securely decommissioned.
Download the Entrust KeyControl Flyer.
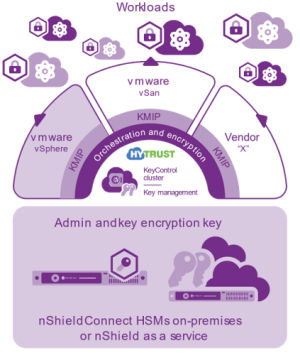 Data encryption, multi-cloud key management, and workload security.
Data encryption, multi-cloud key management, and workload security.
Entrust DataControl secures multi-cloud workloads throughout their lifecycle and reduces the complexity of protecting workloads across multiple cloud platforms. This provides greater protection of your organization’s critical and sensitive information while enabling compliance with data privacy regulations.
Managing encrypted workloads can get complex, especially in a multi-cloud environment
Many workloads contain critical data, which has to be protected. Your company’s reputation is at stake, and after a data breach, lawsuits and loss of revenue are a serious concern.
Workloads go through many lifecycles, from staging to deployment, to backup and eventual decommissioning. Each stage poses different risks of potential data theft or other misuse.
Managing encrypted workloads in a multi-cloud infrastructure
DataControl allows you to manage your encrypted workloads across different infrastructures. It works on-premises and with the leading public cloud platforms, as well as with hyperconvergence and storage solutions. With DataControl, you get a centralized and scalable solution to control all your encryption keys. DataControl includes the VMware-certified Entrust KeyControl Key
Management Server (KMS).
Download the Entrust DataControl Flyer.
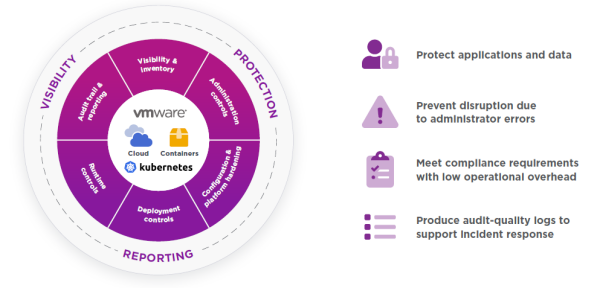
Comprehensive security for hybrid multi-cloud environments
Entrust CloudControl is a powerful solution that reduces risk through visibility and policy. As IT environments transition to hybrid cloud, security architectures must undergo a corresponding transformation. Deploying point solutions that each address a particular infrastructure type just leads to higher costs and inconsistent protection. CloudControl addresses the need for a comprehensive solution by providing a unified framework for security and compliance across the hybrid cloud – reducing both risk and operational overhead. Originally developed as the
industry’s leading solution to protect applications and data in VMware virtualized datacenters, CloudControl also delivers security for public cloud and containerized environments.
Solution highlights
Download the Entrust CloudControl Flyer.



info@ergonomics-europe.com | sales@ergonomics-europe.com
+41 58 311 1000
Ergonomics AG | Uetlibergstrasse 132 | CH-8045 Zürich | Switzerland